Access Backend Resources⚓︎
When the nextAuth Mobile SDK is used to login into the app itself, i.e. through an AppLogin, one can use the webNonce associated with this session for accessing backend resources securely. Alternatively, and if configured in the nextAuth server, one can also request a (OAuth 2.0, OIDC or other) token directly.
webNonce⚓︎
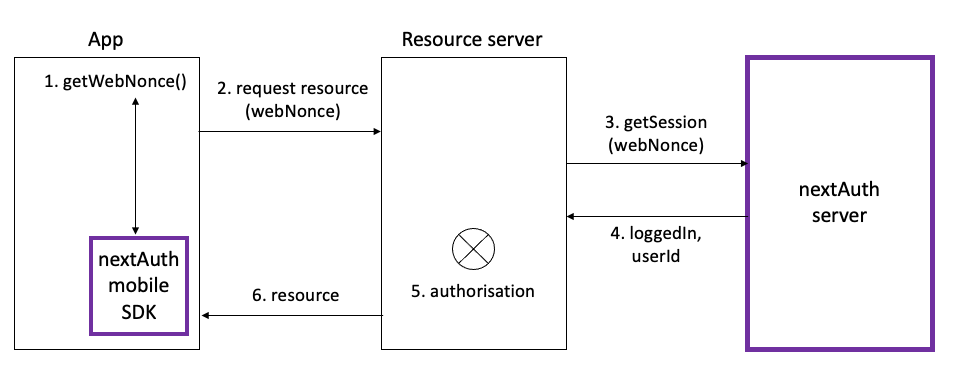
The app can request the webNonce from the nextAuth Mobile SDK (when the user is logged in).
String webNonce = NextAuth.getNextAuth().getAppLogin().getWebNonce();
NextAuth.AppLogin.session?.webNonce
Then, the app can request resources at a resource server using the webNonce associated with the current AppLogin. The resource server then calls getSession from the nextAuth Server's API to learn whether or not the session associated with the given webNonce is currently logged in, and if so, which user is logged in for this session. Based on the userId from the nextAuth Server and internal access management rules, the resource server will determine whether the user is authorised to access the requested resource, and if so, return the resource to the app.
Note
The actual implementation of the communication with the resource server and the resource server itself are outside the scope of nextAuth. The only requirement is that the resource server should be able to make the getSession call to your instance of the nextAuth Server. nextAuth does recommends to use TLS to communicate with the resource server and pin the resource server's public key inside your app.
Exchange webNonce for a Token⚓︎
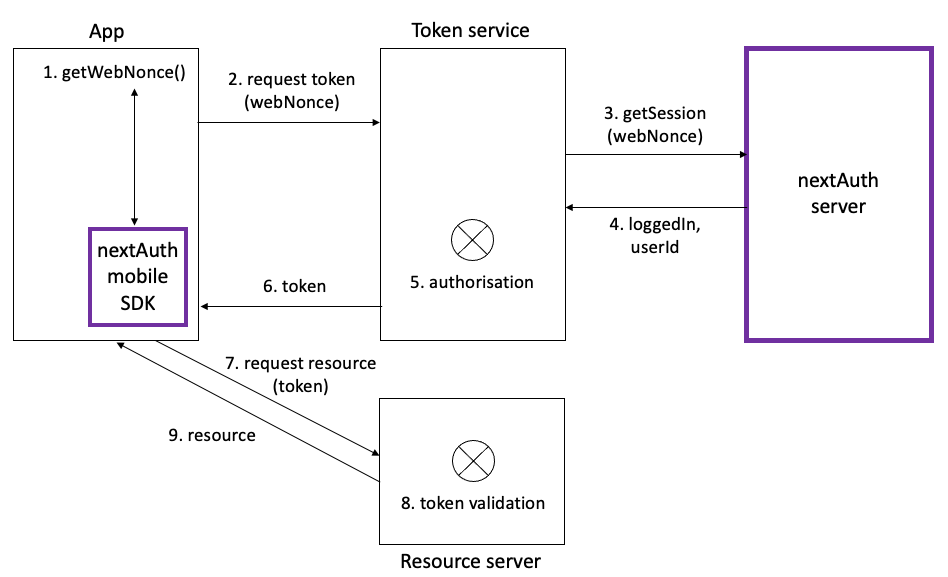
If one or more backends to retrieve data from, cannot communicate with the nextAuth server directly, it is a good idea to implement one or more (OIDC, OAuth 2.0 or other) token service endpoints, which communicate with the nextAuth Server and can hence check that there is someone logged in for the given webNonce. In this scenario, the app then first requests a (OIDC, OAuth 2.0 or other) token based on the webNonce at the token service and then uses the received token to retrieve data from the backend(s).
Note
The actual implementation of the communication with the token service and resource server, as well as the token service and resource server themselves are outside the scope of nextAuth. The only requirement is that the token service should be able to make the getSession call to your instance of the nextAuth server. nextAuth does recommend to use TLS to communicate with the token service and resource server and pin the token service's and resources server's public keys inside your app.
PKCS for OAuth 2.0 Tokens
Even though the exchange of a webNonce for an OAuth 2.0 token can be viewed as the exchange of an authorization code for an OAuth 2.0 token, implementing PKCE (Proof Key for Code Exchange by OAuth Public Clients) will not provide any security benefit. The webNonce arrives directly in the app through the nextAuth Mobile SDK, which also handles user authentication, and hence cannot be intercepted by another (malicous) app. Therefore, nextAuth advises against the use of PKCE for this use case.
Token Validation
Token validation at the resource server typically entails validating the signature on the JWT token (please also verify that the signature algorithm is what you expect it to be). Hence the resource server is sure that the user was logged in at the moment the token was created. If the resource server wants to be sure that user is still logged in at the time of requesting the resource, it could validate the token with the token service, i.e., check if the token has not been revoked. When token validation also includes communication with the token service, nextAuth advises against the use of tokens and recommends to work directly with the webNonce as described before.
Token⚓︎
This feature was made available in v1.2.0 (Android), v1.4.0 (iOS) of the nextAuth Mobile SDK and v2.4.0 of the nextAuth Server.
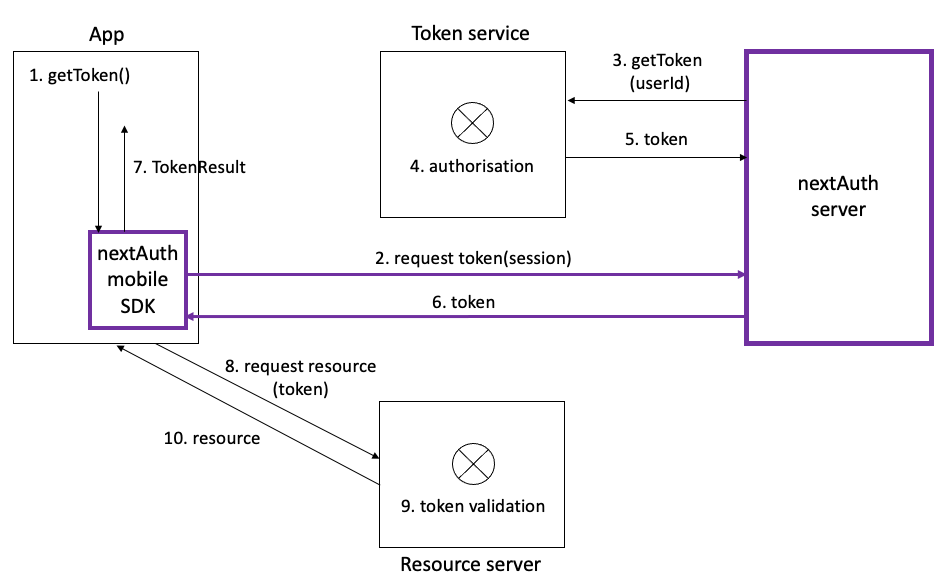
Instead of exchanging a webNonce from the nextAuth Mobile SDK for an AppLogin (which is logged in) and exchanging this in the app for a token, a token can be obtained directly from the nextAuth Mobile SDK if this has been configured in the nextAuth Server. Note that this token is returned asynchronously, i.e., the app should listen for a TokenResult callback. The Token returned by the nextAuth Mobile SDK is the exact answer the nextAuth Server gets from the token service. This is often a JSON object that contains the expiry and the actual access_token that is needed to access resources at the resource server. An example can be found below.
{
"token_type": "Bearer",
"expires_in": 3600,
"access_token": "eyJraWQiOiJ3UHdvd.....gkJktHWp4YeLBGRxInAP2n4OpK6g1LmtNsEZw",
"scope": "openid"
}
NextAuth.getNextAuth().getAppLogin().getToken();
@Override
public void onCallback(Callback callback) {
if (callback instanceof TokenResult) {
Token token = ((TokenResult) callback).token;
// Raw bytes as received by the nextAuth server
token.getRawBytes();
// Raw bytes encoded as UTF-8 String
token.getRawString();
// JSON object from the UTF-8 String (if JSON)
token.getJSON();
// String attribute contained in the JSON object (if JSON)
token.getStringAttribute(attributeName);
// int attribute contained in the JSON object (if JSON)
token.getIntAttribute(attributeName);
}
}
NextAuth.default.getToken(for: session)
func nextAuth(_ nextAuth: NextAuth, didReceive token: Token) {
// TODO: Handle the received upstream token
}
Note
The actual implementation of token service is outside the scope of nextAuth. However, the token service (or a proxy in between) should implement a getToken method and return a token according to the nextAuth specifications (please contact support). An example implementation of a token service proxy can be found at https://git.nextauth.com.